But computer risks are harder to handle than physical ones

It sounds as if it was named by a seven-year-old boy and looks like a film set. Housed in a sleek black truck, ibm’s “x-Force Command Cyber Tactical Operations Centre” travels from city to city, simulating the experience of falling victim to a cyber-attack. Rows of desks sport monitors and keyboards in a room dominated by three giant video-screens. A control room houses server equipment that allows ibm’s staff to simulate a corporate network—and then throw all manner of digital mischief at it. Teenagers “understand what’s going on straight away”, says Caleb Barlow, who runs the show. Board members at big companies enjoy a visit, too: “It’s so different from what they usually do.”
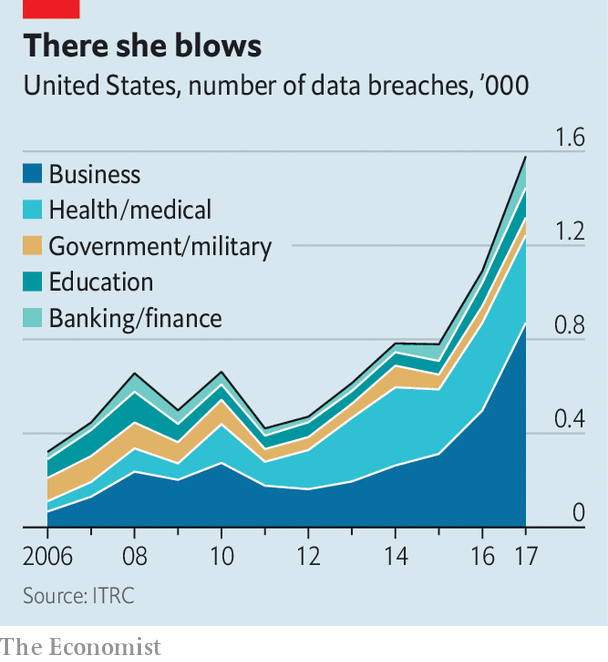
But their interest is not merely recreational. Companies are increasingly worried about the threats lurking in their computer systems. A survey in 2018 by kpmg and Harvey Nash, a firm of headhunters, found that only a fifth of it bosses thought their firm was well prepared for an attack.
That gloomy assessment is borne out by high-profile hacks. In November Starwood, a hotel chain owned by Marriott International, reported that half a billion customer records had been stolen. Magecart, a hacker group, is the chief suspect in the theft of the credit-card information of customers of Ticketmaster, an American firm, Newegg, a computer retailer, and British Airways. In 2017 WannaCry and NotPetya, two malware programs, scrambled files in organisations across the world. Maersk, a Danish shipping firm, said it had suffered costs of $300m. Snafus can be as damaging as attacks. In April tsb, a British bank, botched a computer upgrade and locked millions of customers out of their accounts.
Such mishaps are feeding a fast-growing market for specialist cyber-insurance. Solid numbers are in short supply, but Munich Re, a reinsurer, reckons that a market that wrote $4bn of premiums in 2018 could be writing $8bn-9bn by 2020. Rob Smart of Mactavish, a firm that works with big British insurers, says that “almost all” the firms’ clients have inquired about cyber-insurance in the past couple of years. Insurers are scrambling to hire scarce specialists. Two former directors of gchq, Britain’s electronic-spying organisation, have found jobs advising the industry.
The market is most developed in America, says Robert Hannigan, one of those ex-gchq bosses, thanks in part to Californian laws passed in 2003 that compel firms to confess to large data breaches. These have been copied by other states. But Europe is catching up, says Joseph Ahern of the Association of British Insurers, partly because of privacy and reporting laws that are now stricter than America’s. The need for robust insurance will only grow as companies become more reliant on computers, hackers get more cunning and regulators take an increasingly dim view of lax security. But the unique nature of cyber-risks makes them hard for the insurance industry to handle. In the worst case, they could blow up the nascent market altogether.
The policies on offer so far tend to vagueness, says Mr Smart, and vary widely regarding which risks are covered. That makes companies skittish, he says, and some big clients have decided not to buy insurance as a result. As the industry matures, no doubt policies will become clearer and more standard. But other problems are potentially longer-lasting.
That of working out who was behind a particular hack has already made the news. Mondelez, an American food company hit by the NotPetya malware, is suing Zurich, a big insurance firm, for refusing to pay out under a general insurance policy. Zurich cites an exclusion clause for losses related to war, on the ground that the NotPetya attack is thought to have been carried out by Russia. Even a technologically sophisticated government would have trouble proving such a claim to the standard demanded by a court, says Andrew Coburn of Risk Management Solutions, a consultancy. But if Zurich does win, it could cast a chill across the entire market—unless insurers accept that cyber-insurance may involve shouldering the sorts of risks they have previously sought to avoid.
At the same time, cyber-security risks are inherently tricky to price. All software contains bugs, some of which will cause security weaknesses. But many lurk unknown until a hacker starts exploiting them. Cyber-risks are so new that insurers have only limited data, and the pace of technological change means that what they have quickly goes stale. “In a flood, we know the ways in which water can damage things,” says Shannan Fort of Aon, an insurance broker. “And that’s not likely to change in the next five to ten years. But the way we use technology has changed fundamentally just over the past decade.”
Perhaps the biggest difficulty for insurers is that the risks posed by cyber-attacks are not independent of each other. If an oil refinery in Texas floods, that does not mean one in Paris is any more likely to do so. Insurers build that independence into their risk models, and depend upon it in their calculations of the maximum they may have to pay out in a single year. But a newly found flaw in software can make all users vulnerable simultaneously. Insurers fret that a single big attack could hit many of their clients at once. In the worst case, the value of claims might be more than they could meet.
The WannaCry malware of 2017 illustrates the point. Armed with a software vulnerability stolen from the National Security Agency, gchq’s American counterpart, it infected a quarter of a million computers in 150 countries in just a few days. Its spread was slowed only by luck. Marcus Hutchins, a security researcher later arrested on an unrelated matter, gained access to the malware’s control system that allowed him to shut it off. Whether the industry can figure out a way to deal with such “risk aggregation” is an open question. As one insider says, it “sort of breaks the whole concept of insurance a bit”.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.